Cybersecurity Overview
What is Cybersecurity?
There was a time when the biggest threat to a business was someone breaking in.
Today, the threat comes through emails,or phone calls designed to trick people. And data has become the gold bad actors are after.
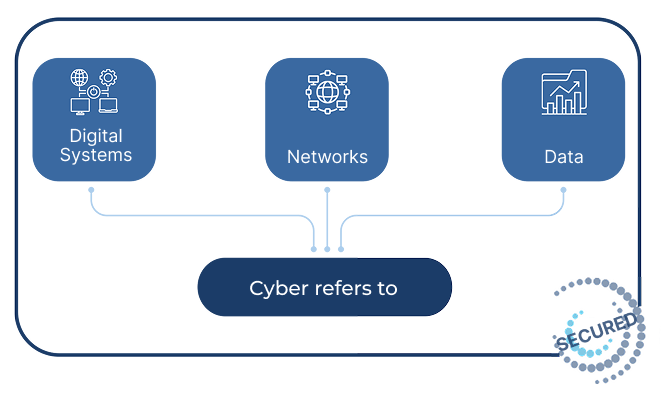
Here, we meet cybersecurity. Cyber refers to digital systems, networks, and data. Security is about protecting them. Put together, cybersecurity is the practice of defending digital assets from unauthorized access, manipulation, and exploitation.
Whether it’s someone stealing customer data, disrupting operations, or holding systems for ransom, the goal of cybersecurity is simple: keep the bad actors out and protect your data.
Below, we’ll explore each stage outlined by the framework.
But Why Do Organizations Still Get Hacked?
Today’s systems are sprawling, interconnected, and constantly changing. What worked to secure your network last year might not hold up today.
Which means cybersecurity teams juggle multiple priorities, often without enough resources or specialized knowledge to stay ahead of the threats. This is how system vulnerabilities arise.
Effective cybersecurity is about having a defense system that recognizes and adapts to evolving cyberthreats. This requires resources, specialized personnel, and domain expertise.

MITRE ATT&CK Framework
The MITRE ATT&CK Framework was developed in 2013 by the MITRE Corporation. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge, and it’s one of the most widely used models to understand how cyberattacks unfold.
Think of it as a map of how attackers operate. It breaks it down, step by step, into the exact tactics and techniques hackers use to breach, persist, and cause damage.
Let’s walk through each stage and see how a modern cyberattack unfolds.
- Privilege Escalation
- Defense Evation
- Credential Access
- Recon
- Weaponization
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evation
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
Prepare
Before launching an attack, attackers spend time learning about their target. This phase is all about understanding systems, identifying weaknesses, and preparing custom payloads designed to exploit them.
Recon
Every attack starts with a question: what’s vulnerable? Reconnaissance is where attackers look for answers. Their goal here is simple: learn as much as possible without raising alarms.
Passive reconnaissance involves collecting publicly available data without interacting with the system:
- Scanning social media and corporate websites to identify key employees, technologies in use, or third-party vendors.
- Searching DNS records or WHOIS databases to understand infrastructure details and spot leaked credentials.
Active reconnaissance is a direct probe for system vulnerabilities:
- Conducting network scans to detect open ports and exposed services.
- Using banner-grabbing techniques to identify software versions and operating systems.
Weaponization
Once enough is known, the attacker builds the weapon. This could be custom malware that exploits a specific vulnerability.
It could be a malicious script hidden inside a document or a zero-day exploit, i.e., a vulnerability only the attacker has discovered.
Deliver
Once the planning is done and the payload is ready, the attacker shifts focus to getting in. Attackers use phishing, stolen credentials, or software vulnerabilities to break in, and once inside, they make sure they can stay.
Initial Access
Before anything can happen, the attacker needs to get in. This is the stage where bad actors gain unauthorized access to systems. Common access techniques include:
- Phishing, where users are deceived into opening malicious links or infected attachments.
- Exploiting unpatched software, using known flaws to bypass defenses.
- Using compromised credentials acquired from past breaches or the dark web.
Execution
Once inside, attackers start direct interaction with the compromised systems to activate their attack. Their techniques often involve:
- Running scripts using tools like PowerShell, Python, or Bash to carry out commands.
- Exploiting software bugs to escalate code execution privileges.
- Embedding malware into processes or user files.
Persistence
To maintain access over time, even after reboots or security updates, attackers implement persistence mechanisms.
They install backdoors, create hidden user accounts with admin privileges, and slip in malware that ensures continued access, even if initial entry points are closed.
Exploit
For an attacker to do real damage or to move through systems unnoticed, they need more access and fewer obstacles. This stage is about gaining control, staying hidden, and using stolen credentials to operate like insiders.
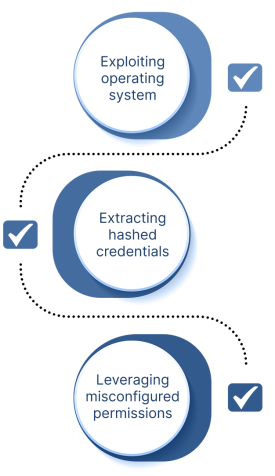
Privilege Escalation
Many attacks require elevated permissions to reach sensitive assets. Privilege escalation allows attackers to move from basic access to admin or root-level control.
Defense Evasion
The longer an attacker stays unnoticed, the more control they gain. Their goal is to avoid alerting detection systems, antivirus tools, and cybersecurity threat monitoring platforms.
They encrypt or disguise their code so it doesn’t match known threat signatures.
To the outside world, everything seems normal, but the attack keeps running quietly in the background.
Methods of Privilege Escalations
Credential Access
Attackers go after credentials because they unlock unrestricted access across the compromised system.
They can be harvested through keyloggers that watch every keystroke, dumped from memory, browsers, or files where they were left behind.
Once they have legitimate credentials, they no longer look like intruders. They look like users. Which means they can gain admin privileges and exploit without raising alarms.
Control
With access and knowledge, attackers explore the environment to identify high-value assets spread across systems. They want to know what’s worth taking, where it’s kept, and how to reach it without setting off alarms.
Discovery
You can’t take what you can’t find. So attackers start mapping the compromised system. Discovery helps them map out infrastructure, identify key assets, and refine their attack plan. Common activities in this stage include:
- Network scanning to identify hosts, services, and connections.
- Querying configurations to uncover patch levels and exposed vulnerabilities.
- Identifying privileged users and critical systems that contain high-value data.
Lateral Movement
With internal knowledge and credentials in hand, attackers expand their presence across the network. Lateral movement spreads the attack to additional systems using techniques such as:
- Using remote desktop tools like RDP or SSH to move between systems while impersonating users.
- Leveraging pass-the-hash or pass-the-ticket methods to authenticate without needing plaintext credentials.
- Exploiting trust relationships between systems to bypass segmentation controls.
Collection
In this stage, attackers gather the sensitive data identified during earlier stages. This could involve intellectual property, financial records, or personal information.
They capture keystrokes, take screenshots, and run scripts that pull emails, documents, or database entries. Then they organize the files so they can be moved quickly when the time comes.
Execute
This is where the breach becomes visible. Once attackers are in control and have what they require, it’s time to act. They communicate with the systems they’ve compromised remotely, move the stolen data out, and trigger the final blow.
Command and Control (C2)
To manage ongoing cyber intrusions, attackers establish a remote communication channel with compromised systems. This is a way to issue instructions, update malware, or pull data.
This connection is often encrypted, hidden inside everyday traffic like HTTPS or DNS. Sometimes, they’ll use familiar services like cloud apps or social media platforms, so nothing looks suspicious.
That’s why this stage is crucial because without C2, attackers lose control over the compromised systems.
Exfiltration
With data collected and control established, the focus shifts to transferring information out of the environment, typically over a period of time.
Attackers rarely dump everything at once. They compress the files, encrypt them, and send them out in pieces. The goal is to avoid detection, stay under the radar, and blend in with normal system behavior.
The method doesn’t matter as much as the outcome: valuable data leaves the building.
Impact
The final step isn’t always about money. Sometimes, it’s about damage. Ransomware might lock down the systems, demanding payment to restore access, or leak sensitive data. This is where the attacker’s objective becomes clear, and for the victim, the consequences come fast.
Where Cybersecurity Falls Short Today
The problem is fragmentation.
Most organizations aren’t ignoring cybersecurity; they’re overwhelmed by it. Security teams today are tasked with protecting a growing web of endpoints, firewalls, internal apps, databases, APIs, and cloud infrastructure. Each of these components generates its own type of data, requires its own tooling, and often demands different kinds of expertise.
Two major problems with cybersecurity
Teams end up with too many dashboards, too many alerts, and too little time to take note of everything. Threats slip through, and triaging happens too late, if it happens at all. As a result, even well-resourced security teams find themselves reactive instead of proactive. Because the signals get buried in the noise, and attackers get better at taking advantage of that delay.
To fix this, cybersecurity measures require clarity, customizations, and, above all, data.
Observata’s Cybersecurity Approach
We believe cybersecurity shouldn’t be isolated from the systems it’s meant to protect.
You can have the best security tools guarding your organization, but if you can’t see how they’re interacting with your systems, you’re working blind. To take proactive action, you require all the data from various system components and analyze it.
Observability fills this gap—but only if it’s tightly integrated with cybersecurity operations.
For this, expertise in both domains is crucial. Observability provides real-time visibility into your internal operations to spot issues before they metastasize. Cybersecurity helps you patch these issues that could be exploited and stay ahead of evolving cyberthreats.
This connected view helps organizations answer critical questions faster. For example:
- Is a slowdown the result of poor code or a live threat?
- Are failed logins just user error or a credential-stuffing attempt?
- Is the data transfer a routine sync or a breach in progress?
When both cybersecurity and observability measures are aligned, teams can preempt, validate, and respond to issues with speed and clarity.
Fortify Your Digital Environment
Our cybersecurity service, HYPR Guard, is built around this philosophy. Powered by CrowdStrike, it protects endpoints, identities, cloud workloads, and insider threats.
This unified approach eliminates the challenges of fragmented tools and inconsistent data, offering seamless scalability across diverse infrastructures.
HYPR Guard combines CrowdStrike’s platform with Observata’s expert team to provide proactive threat management, incident response, ongoing tuning, and training.
We handle the complexity. You get the clarity and security.